I was trying to import a new certificate with an SSL key, but it was without success.
But as usual, before trying that on production, I tried that on my lab setup. It was done without any problems.
But when trying with the production Alteon, running the same 29.5.1 version, I got this message:
> -----END RSA PRIVATE KEY-----
Enter key passphrase:
Error: The private key is not a valid RSA key
Error: Failed to extract key XXXXX
After trying it several times, comparing some random strings inside the key I noticed a lag when I pasted the key to the production Alteon. The reason for the lag was SecureCRT that was configured to insert delays between keys. This feature is extremely useful with pasting large text into NX-OS.
My lab setup is with the default Line Send delay of 5ms and Character send delay of 0ms.
So I tried to use the lap SecureCRT delay setup on my production Alteon, and to my surprise it worked!
So to sum up: when pasting to Alteon 29.5.1, you better use the default SecureCRT delay settings.
One more thing and this will save you precious time digging through the command reference:
"key" and "srvrcert" names must be identical
Showing posts with label ssl. Show all posts
Showing posts with label ssl. Show all posts
Tuesday, November 4, 2014
Friday, September 12, 2014
HTTP to HTTPs redirect with a twist
Lab goal
Create a new VIP/virt - 10.136.85.13.
The main page should be using HTTP but all the other elements should be using SSL.
The main page should be using HTTP but all the other elements should be using SSL.
Setup
I'll use my Loadbalancer Lab Setup.
The loadbalancer is Radware's Alteon VA version 29.5.1.0
The initial Alteon VA configuration can be found here.
Alteon configuration
We will reuse group 10 which includes all web servers.
So all is left is to create a VIP/virt with services HTTP and HTTPS
Lines 8-10 - Source NAT. Without it traffic from the server will go directly to client without going first through the Alteon.
Now for the AppShape script:
So all is left is to create a VIP/virt with services HTTP and HTTPS
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 | /c/slb/virt 86_13
ena
ipver v4
vip 10.136.85.13
/c/slb/virt 86_13/service 80 http
group 10
rport 80
/c/slb/virt 86_13/service 80 http/pip
mode address
addr v4 10.136.85.200
/c/slb/virt 86_13/service 443 https
group 10
rport 443
/c/slb/virt 86_13/service 443 https/pip
mode address
addr v4 10.136.85.200
|
Lines 8-10 - Source NAT. Without it traffic from the server will go directly to client without going first through the Alteon.
Now for the AppShape script:
1 2 3 4 5 6 7 8 9 10 11 12 | when HTTP_REQUEST { # exctract the fields from the HTTP headers set url [HTTP::uri] set host [HTTP::host] if {[string equal $url "/"] ==0} { HTTP::redirect "https://$host$url" 301 } } -----END |
- Line 7 checks if the path is not /" and then:
- Line 8 Redirect all requests to the page elements, such as pictures, iFrames and CGI-BIN to HTTPS
- Notice that the redirect was built with the extracted host name and the URL
Next lets import and apply the AppShape++ script:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 | /c/slb/appshape/script redirect_to_https
ena
import text
when HTTP_REQUEST {
# exctract the fields from the HTTP headers
set url [HTTP::uri]
set host [HTTP::host]
if {[string equal $url "/"] ==0} {
HTTP::redirect "https://$host$url" 301
}
}
-----END
/c/slb/virt 86_13/service 80 http/appshape
add 10 redirect_to_https
|
Test
It looks like a regular HTTP page, but notice the TCP port being used inside the iFrame. Its 443, which is HTTPS.Success!
Summary
This exact setup can be done with crule,but I think that using AppShape++ is much easier to understand, as you see the condition and the action in one place.
Thursday, September 4, 2014
AppShape++ and SSL offloading
After running my fist AppShape++ script, I was wondering if it will work with SSL offloading as well.
Lets try it out, using my lab setup again, and I'll be adding on top my previous lab.
First I'll need to create SSL policy on the Alteon VA version 29.5.1.0:
/c/slb/ssl/sslpol mySSL_Pol
cipher "high"
ena
This will select only high security encryption and integrity algorithms.
Next we need to create a self signed certificate:
>> LB1 - SSL Policy mySSL_Pol# /cfg/slb/ssl/certs/srvrcert
Enter server certificate id: mySRV_Cert
------------------------------------------------------------------
[Server certificate mySRV_Cert Menu]
name - Set descriptive certificate name
generate - Create or update self-signed server certificate
del - Delete server certificate
cur - Display current server certificate configuration
>> LB1 - Server certificate mySRV_Cert# gen
This operation will generate a self-signed server certificate.
Enter key size [512|1024|2048|4096] [1024]: 2048
Enter server certificate hash algorithm [md5|sha1|sha256|sha384|sha512] [sha1]: sha256
Enter certificate Common Name (e.g. your site's name): *.dans-net.com
Use certificate default values? [y/n]: y
Enter certificate validation period in days (1-3650) [365]: <enter>
....
Self signed server certificate, certificate signing request and key added.
We also need to enable SSL globally:
/cfg/slb/ssl/on
Now lets add SSL offloading to virt 6_10:
/c/slb/virt 6_10/service 443 https/ssl
srvrcert cert mySRV_Cert
sslpol mySSL_Pol
/c/slb/virt 6_10/service 443 https/appshape
add 10 group_by_host
Notice that not only SSL offloading was added, but also we applied the AppShape++ script.
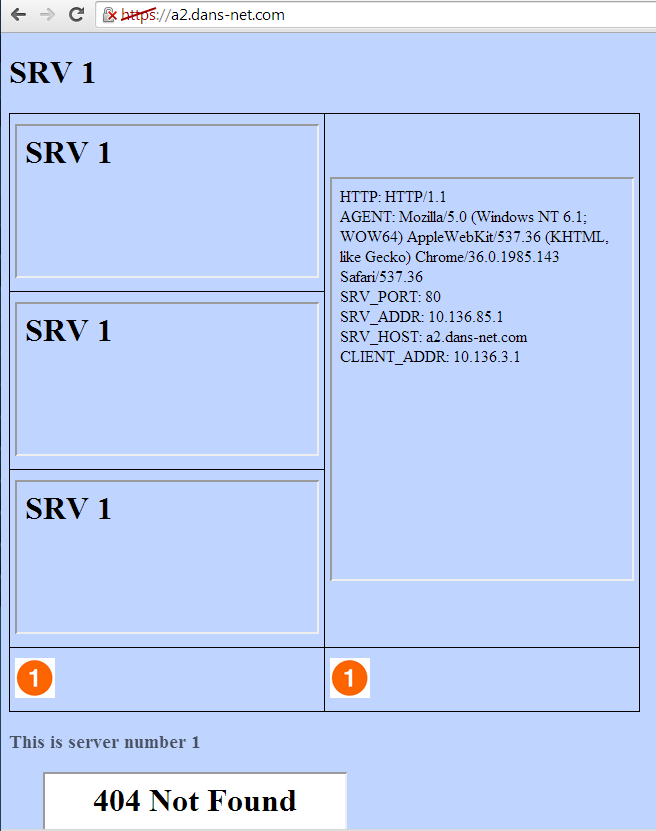
Lets try it out:
Notice that the background is still blue, which means its HTTPS and that the SRV_PORT is 80, so we really have SSL offloading and the AppShape++ script works with SSL offloading too.
So yes! AppShape++ works also when using SSL offloading.
Lets try it out, using my lab setup again, and I'll be adding on top my previous lab.
First I'll need to create SSL policy on the Alteon VA version 29.5.1.0:
/c/slb/ssl/sslpol mySSL_Pol
cipher "high"
ena
This will select only high security encryption and integrity algorithms.
Next we need to create a self signed certificate:
>> LB1 - SSL Policy mySSL_Pol# /cfg/slb/ssl/certs/srvrcert
Enter server certificate id: mySRV_Cert
------------------------------------------------------------------
[Server certificate mySRV_Cert Menu]
name - Set descriptive certificate name
generate - Create or update self-signed server certificate
del - Delete server certificate
cur - Display current server certificate configuration
>> LB1 - Server certificate mySRV_Cert# gen
This operation will generate a self-signed server certificate.
Enter key size [512|1024|2048|4096] [1024]: 2048
Enter server certificate hash algorithm [md5|sha1|sha256|sha384|sha512] [sha1]: sha256
Enter certificate Common Name (e.g. your site's name): *.dans-net.com
Use certificate default values? [y/n]: y
Enter certificate validation period in days (1-3650) [365]: <enter>
....
Self signed server certificate, certificate signing request and key added.
We also need to enable SSL globally:
/cfg/slb/ssl/on
Now lets add SSL offloading to virt 6_10:
/c/slb/virt 6_10/service 443 https/ssl
srvrcert cert mySRV_Cert
sslpol mySSL_Pol
/c/slb/virt 6_10/service 443 https/appshape
add 10 group_by_host
Notice that not only SSL offloading was added, but also we applied the AppShape++ script.
Lets try it out:
Notice that the background is still blue, which means its HTTPS and that the SRV_PORT is 80, so we really have SSL offloading and the AppShape++ script works with SSL offloading too.
So yes! AppShape++ works also when using SSL offloading.
Subscribe to:
Posts (Atom)