Some ACLs are short, some ACLs are really long!
Here is a question, would any to 8.7.109.176 port 443 match any of the ACEs?
With dt_aclcheck.tcl, it is easy:
IOU1#tclsh unix:dt_aclcheck.tcl 100 tcp any 8.7.109.176 1234 443
01
950 permit tcp any host 8.7.109.176 eq 443
4040 permit tcp any any established
How about icmp?
IOU1#tclsh unix:dt_aclcheck.tcl 100 icmp any any
01
4010 deny icmp any any echo
4020 deny icmp any any traceroute log
4030 permit icmp any any
4160 deny ip any any
Here is the syntax for the command:
IOU1#tclsh unix:dt_aclcheck.tcl
Usage - dt_aclMatch.tcl <acl_name> <protocol> <source IP> <destination IP> [source port] [destination port]
Grab the file HERE, and upload it to the router. Enjoy!
And let me know if you need any help with this.
Showing posts with label ios. Show all posts
Showing posts with label ios. Show all posts
Thursday, March 10, 2016
Thursday, September 24, 2015
Embedded packet capture and interface ACLs and Zone Based Firewall
Cisco IOS Embedded packet capture is a great tool for trouble shooting. Very similar to the ASA capture command.
It could be better, as it won't parse the packets as good as tpcdump, but it is way better than nothing.
However I couldn't figure out what the order of operation, with regards to ACLs and ZBF.
So I labbed it up, with IOU 15.4, and here are the results:
So it looks like the embedded packet capture is placed at the right place, right before incoming ACL/ZBF check. However more testing needed to be done: NAT, outgoing ACL/ZBF, IPS drops, encryption, sanity checks
I wish Cisco would have published an official and full "order of operation". Here is the best I have found so far.
FYI....
It could be better, as it won't parse the packets as good as tpcdump, but it is way better than nothing.
However I couldn't figure out what the order of operation, with regards to ACLs and ZBF.
So I labbed it up, with IOU 15.4, and here are the results:
- For incoming ACL, packets are captured before ACL is evaluated
- For incoming ZBF policy, packets are captured before the policy is checked.
So it looks like the embedded packet capture is placed at the right place, right before incoming ACL/ZBF check. However more testing needed to be done: NAT, outgoing ACL/ZBF, IPS drops, encryption, sanity checks
I wish Cisco would have published an official and full "order of operation". Here is the best I have found so far.
FYI....
Monday, January 26, 2015
VIRL - A slow greatness
I had a migration project from 6500 to ASRs. I have decided to check out VIRL.
My migration setup requires 14 routers and a test server. Reading the system requirements for such a setup made me decide not to install on my laptop.
I went ahead and installed it on a not so small ESX server: A new UCS machine (24 cores, 380G memory, running 4 VMs, including VIRL), ESX 5.1.
I have allocated VIRL 4vCPU, 16GB memory.
The installation was not that short, but not that hard either. After the installation was over, I installed VM Maestro and started building my lab. Working with VM Maestro, which is VIRL's GUI, was really easy. The only annoying thing was my inability to set the interface numbers for the connections between routers.
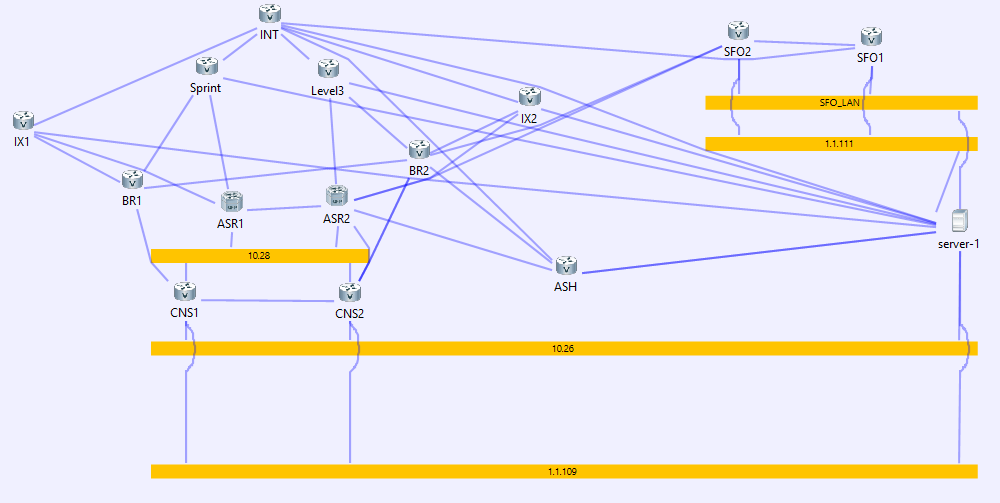
Here is how my final setup looks like:
The setup is running 12 vIOS, 2 CSR1K, and one Ubuntu server, from where I ran my automated tests.
I pressed on "Start simulation" and then when trouble started. It took about 40 minutes for all the routers to load. Then the CLI felt like 2400 baud. It was crawling!
Notice that each time you start the simulation, for example after adding or removing a link, all the routers are rebuild from scratch. They are not just powered on. They are cloned from a template and go through lengthy installation process. Especially the ASRs which take forever to install themselves.
So I tried to run just 4 routers. That was working well and everything was snappy.
Then I tried to upgrade the VM to 6 vCPUs. Now it took just 3 minutes to load all the routers. The CLI felt much better at 9600 baud.
Then I tried to upgrade the VM to 8 vCPUs. Now everything works almost as fast as GNS3 with IOU!
After setting up the lab foundation, it was time actually to start configuring the lab. I have configured OSPF and BGP. Everything worked, but the response time was slower. Although the response time was slower, the lab was very usable.
To run the test, I am using some VRF magic and bash scripting on the Linux machine. I think it worth a blog entry on its own. Then after 30 minute of stepping away from the lab, I noticed that most OSPF and BGP sessions were lost. I had to press "enter" several times on each router's prompt to wake everything up:
Just when I wake the routers:
After 30 minutes:
My migration setup requires 14 routers and a test server. Reading the system requirements for such a setup made me decide not to install on my laptop.
I went ahead and installed it on a not so small ESX server: A new UCS machine (24 cores, 380G memory, running 4 VMs, including VIRL), ESX 5.1.
I have allocated VIRL 4vCPU, 16GB memory.
The installation was not that short, but not that hard either. After the installation was over, I installed VM Maestro and started building my lab. Working with VM Maestro, which is VIRL's GUI, was really easy. The only annoying thing was my inability to set the interface numbers for the connections between routers.
Here is how my final setup looks like:
The setup is running 12 vIOS, 2 CSR1K, and one Ubuntu server, from where I ran my automated tests.
I pressed on "Start simulation" and then when trouble started. It took about 40 minutes for all the routers to load. Then the CLI felt like 2400 baud. It was crawling!
Notice that each time you start the simulation, for example after adding or removing a link, all the routers are rebuild from scratch. They are not just powered on. They are cloned from a template and go through lengthy installation process. Especially the ASRs which take forever to install themselves.
So I tried to run just 4 routers. That was working well and everything was snappy.
Then I tried to upgrade the VM to 6 vCPUs. Now it took just 3 minutes to load all the routers. The CLI felt much better at 9600 baud.
Then I tried to upgrade the VM to 8 vCPUs. Now everything works almost as fast as GNS3 with IOU!
After setting up the lab foundation, it was time actually to start configuring the lab. I have configured OSPF and BGP. Everything worked, but the response time was slower. Although the response time was slower, the lab was very usable.
To run the test, I am using some VRF magic and bash scripting on the Linux machine. I think it worth a blog entry on its own. Then after 30 minute of stepping away from the lab, I noticed that most OSPF and BGP sessions were lost. I had to press "enter" several times on each router's prompt to wake everything up:
Just when I wake the routers:
16:54:20 +++++-+---+-+---+--++++--++--+-+++++++++
16:54:33 +++++++++++++++++++++++--+++++++++++++++
16:54:36 +++++++++++++++++++++++--+++++++++++++++
16:54:40 ++++++++++++++++++++++++++++++++++++++++
16:54:42 ++++++++++++++++++++++++++++++++++++++++
16:54:43 ++++++++++++++++++++++++++++++++++++++++
16:54:45 ++++++++++++++++++++++++++++++++++++++++After 30 minutes:
17:21:53 ++++++++++++++++++++++++++++++++++++++++
17:21:55 ++++++++++++++++++++++++++++++++++++++++
17:21:56 ++++++++++++++++++++++++++++++++++++++++
17:21:58 ++++++++++++++++++++++++++++++++++++++++
17:22:00 ++++++++++++++++++++++++++++++++++++++++
17:22:01 ++++++++++++++--+------++++--+--+-++++++
time 111112222222333333444445555666677788899B
%H:%M:%S 589BC34679BC4679BC679BC89BC79BC9BC9BCBCC
17:22:17 +++++-----+-----+------++++--+--+-++++++
17:22:40 +++++-----+-----+------++++--+--+-++++++
17:23:02 +++++-----+-----+------++++--+--+-++++++
17:23:24 +++++-----+-----+------++++--+--+-++++++Friday, November 14, 2014
GNS3 - ASAv and XRv and IOU and XEv
I am able to run ASAv and XRv and IOU and XEv on my la;ptop, forming OSPF neighbor relationship between them.
I then pinged each loopback from the ASA and also pinged each loopback from IOU. This test shows:
All thanks for GNS3 v1.1. Isn't it great?
Here is the topology:
And here is some show commands from the ASA:
GNS3 integration with Virtual box is very useful. Whatever you can run inside Virtualbox, you can connect to each other with endless possibilities.
My system76 laptop is running Ubuntu 14.04, 16GB, i7 and SSDs.
I was using the following resources:
I then pinged each loopback from the ASA and also pinged each loopback from IOU. This test shows:
- One way broadcast and one way unicast are working - ARP
- Unicast is working - ICMP
- Multicast is working - OSPF
All thanks for GNS3 v1.1. Isn't it great?
Here is the topology:
And here is some show commands from the ASA:
GNS3 integration with Virtual box is very useful. Whatever you can run inside Virtualbox, you can connect to each other with endless possibilities.
My system76 laptop is running Ubuntu 14.04, 16GB, i7 and SSDs.
I was using the following resources:
- Install these items from https://github.com/GNS3/
- gns3-gui
- gns3-server
- iouyap
- dynamips (this is needed even if not using dynamips for IOS)
- vboxwrapper
- vpcs (optional, but very handy to test connectivity)
- Virtualbox integration with GNS3 won't work without virtualbox SDK: http://forum.gns3.net/topic6145.html
- Set permissions for dynamips and iouap:
cd /usr/local/bin
sudo setcap cap_dac_override,cap_net_admin,cap_net_raw+eip dynamips
sudo setcap cap_net_raw,cap_net_admin+eip iouap - CSR1K install: http://herdingpackets.net/2014/02/06/using-the-cisco-csr1000v-in-gns3-with-virtualbox/
- XRv install: http://www.noshutdown.ma/ios-xrv-step-step-install-gns3-integration/
Notice the NIC type. It should be MT server.
Notice to set the NIC type in GNS3. GNS3 will override vbox configuration. - XR tutorial for IOS users: http://networkgeekstuff.com/networking/cisco-ios-xr-complete-getting-started-examples-guide/
- How to install ASAv on VMWare workstation: http://brezular.com/2014/07/04/cisco-asav-virtual-appliance-on-vmware-workstation/
- I encounter the following issues:
- IOU console connection get lost: https://community.gns3.com/message/4635?sr=search&searchId=4578100e-e5c1-4653-8be8-83f6c7dcc7b9&searchIndex=1#4635
Should be fixed next version - GNS telnet server and XRv not working. Don't enable "remote console": http://forum.gns3.net/post38696.html#p38696
Should be fixed next version - Sometime I need to disconnect and reconnect the XRv from the switch: http://www.noshutdown.ma/ios-xrv-step-step-install-gns3-integration/
Search for "know issue" in that link.
Tuesday, October 28, 2014
GNS3 1.1
I was never a big fan of GUI tools, so I used dynagen and dynamips for my network designs. But since 15.2 was the last version released for 7200, dynamips is no longer useful (especially for IKEv2 and OSPFv3 stuff)
I was hoping that Cisco would release VIRL, and they promised to do so for the past year and a half, but it looks like it will never come. Shelling out 10K$ for CML (the payed version of VIRL) is a bit too much for most of us. But there is a good alternative:
Not long time ago GNS3 version 1.0 was released and soon after version 1.1. was released too. And after long time of being a backer for their funding campaign I have decided to try GNS3 with IOU.
After installing GNS3 on both linux and windows (vmware required), I found that GNS3 is really easy to use, and that IOU is AMAZING. IOU is sooooo fast, and everything just works(tm). I wish I had it years ago!
Goodbye dynamips and dynagen, and thank you so much.
Hello IOU and GNS3. I know it will be a start of a wonderful friendship :)
Subscribe to:
Posts (Atom)